Newsletter
10.07.2021 | 7'' read
An incomplete nation-state APT landscape
* The most clicked link from last week’s newsletter was Kaspersky’s technical report on the infamous FinSpy surveillance toolset. Report includes discovery of UEFI bootkit for persistence on Windows.
- I’ll be in Atlanta, GA from October 25-28 to speak at this year’s hybrid ICS Cyber Security Conference. ATL folks, let’s grab coffee.
Monday blues.
The NSA’s Rob Joyce is a bit of a rarity in .gov security circles. Over the years, as the NSA’s hacker-in-chief, he embedded himself within the security research community, spoke candidly about nation-state hacking operations (watch the Enigma speech!) and developed a reputation for straight talk in an industry full of hot air.
Last week, Joyce was back at it during a fireside chat at the Aspen Cyber Summit (skip to 3:21) where he outlined the U.S. government’s “sand-and-friction” strategy (read my story) and shared blunt assessments on the capabilities of what he described as ‘the big four’ — China, Russia, Iran and North Korea.
On Russia: “They are the disruptive force. They are very active in the intelligence-gathering activities, still, both against governments [and] critical infrastructure. We’ve seen evidence of pre-positioning against U.S. critical infrastructure. All things that can’t be tolerated and we need to work against.”
On China: “Scope and scale, China is off the charts. The amount of Chinese cyber actors dwarfs the rest of the globe, combined. The high end of the Chinese sophistication is really good.”
On North Korea: “[They’re] very, very focused on creating wealth for the regime because there’s not many more sanctions that the world can put on North Korea. They found that stealing Bitcoin is often easier than stealing from the Bank of Bangladesh. They haven’t been hitting the biggest banks quite as aggressively, because they’re making their money in the crypto space.”
On Iran: “Iran’s still active. Still actively engaged in offensive cyber. But what we’re seeing is they’re often very focused on regional things right now. They haven’t been as focused on broader impact. But they’re capable and most importantly they’re dangerous because they’re less judicious in what they decide is a reasonable action. I think at times Iran doesn’t understand just how much they’ve gone up to, and even over, the line to the point where they’ve drawn the ire and concern of the greater greater community.”
While it’s refreshing to hear the NSA’s take on apex-actors, the session felt incomplete. While nation-state malware attacks from China, Russia, Iran and North Korea make for sexy CNN headlines, they’re not nearly the cream of the crop.
Here’s one of my favorite security conference slide decks from my friend and ex-GReAT colleague Vicente Diaz:
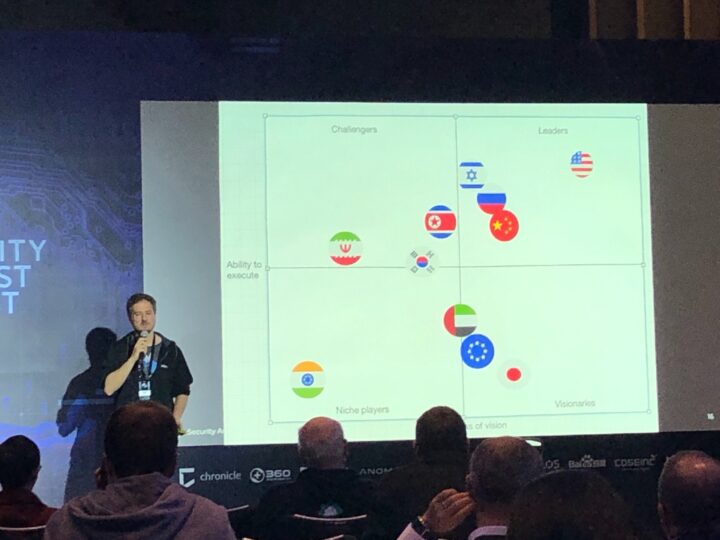
Notice those flags in the top right of the magic APT quadrant? Exactly.
An honest and open discussion about nation-state capabilities and operations must include all the actors, including the U.S., Israel, France, South Korea and the growing list of European nations managing cyber-espionage campaigns.
As the supply chain hacks show, we are all victims and the infection of corporate networks is seen as accepted collateral damage. If we are to embrace sand-and-friction to disrupt adversaries, we can’t only be learning from a handful of “bad” countries. That doesn’t make much sense.
A final thought — It’s tempting for the U.S and its allies to claim moral leadership in the cyber-espionage space but it’s not an entirely honest conversation when you’ve been caught circumventing Windows Update mechanisms (a terrible precedent) and you lost control of your own destructive worm attack.
_ryan
On to the newsletter…
An APT found in Russia.
Speaking of balkanized research disclosures, here’s a doozy from sanctioned Russian security vendor Positive Technologies:
Advertisement — Symmetry Systems.
Using Symmetry DataGuard, cloud-security teams tighten IAM policies around data, incident response teams know precisely what data objects are involved in a breach, and governance teams audit every access across every data store. Get in touch today for a demo.
Offensive security research.
- New from Runa Sandvik, accompanying a presentation at the OBTS conference: Made in America: Green Lambert for OS X.
- Chrome in-the-wild bug analysis: CVE-2021-30632 is a type confusion bug in the JIT compiler of Chrome that can be used to cause remote code execution (RCE) in the renderer of Chrome by a single visit to a malicious site. CVE-2021-30633 is a use-after-free bug in the IndexedDB API of the browser process that can be used to escape the Chrome sandbox once the renderer is compromised by CVE-2021-30632. Together, these two bugs allow a full remote compromise of Chrome (RCE + sandbox escape).
- Hijacking iCloud credentials with Apple Airtags: “An attacker can carry out Stored XSS on this https://found.apple.com page, by injecting a malicious payload into the Airtag “Lost Mode” phone number field. A victim will believe they are being asked to sign into iCloud so they can get in contact with the owner of the Airtag, when in fact, the attacker has redirected them to a credential hijacking page.”
- Randori has released a detailed technical analysis of the nasty VMWare vCenter Server flaw and published indicators-of-compromise to help defenders spot signs of infections.
- Abusing HTTP hop-by-hot request headers: A write-up of techniques that can be used to influence web systems and applications in unexpected ways, by abusing HTTP/1.1 hop-by-hop headers. Systems affected by these techniques are likely ones with multiple caches/proxies handling requests before reaching the backend application.
Phrack is back
- An entire sub-section is required to announce the return of Phrack Magazine. Also, the OffensiveCon CFP is now open.
Supply chain of pain
- While we’re all fixated on the value of SBOMs to help add transparency to the software supply chain, Qualcomm’s Alex Gantman warns that poor metaphors are leading to unrealistic proposals. “In the end, scarce security resources will be diverted to produce compliance make-work with no tangible benefit.”
- Google has rolled out sos.dev, a million-dollar program aimed at rewarding developers for enhancing the security of critical open source projects that we all depend on. The scope isn’t written in stone.
- Google’s Dan Lorenc on a “zero trust supply chain” is very much worth your time. Slides here.
- The VEX (Vulnerability Exploitability eXchange) concept and format was developed to help with SBOMs.
- Here’s a comprehensive public database of supply chain security compromises dating back to 2003.
Security at Redmond.
- Microsoft’s new Windows 11 Security Book is very well done.
- Redmond’s hacker-in-chief David Weston on Windows 11 security and all the hardware security goodness on offer.
- Microsoft has created a four-part docuseries on NOBELIUM, the Russian threat actor behind the SolarWinds mega-hack.
Last-minute leftovers.
- Apache server patch and warning: “This issue is known to be exploited in the wild.”
- Wired’s Andy Greenberg covers a USENIX conference talk on biohackers encoding malware in a strand of DNA.
- ESET has flagged a previously undocumented UEFI bootkit that persists on the EFI System Partition.
- A paper on advancements in homomorphic encryption, the holy grail of privacy engineering.
Tangentially.
- Facebook shares details on the Monday’s outage that also took down Instagram and WhatsApp.
P.S. Full podcast episodes are available on the SecurityConversations.com home page, and on all major platforms. Subscribe directly: Apple/iPhone, Google/Android, Spotify and Amazon/Audible.
